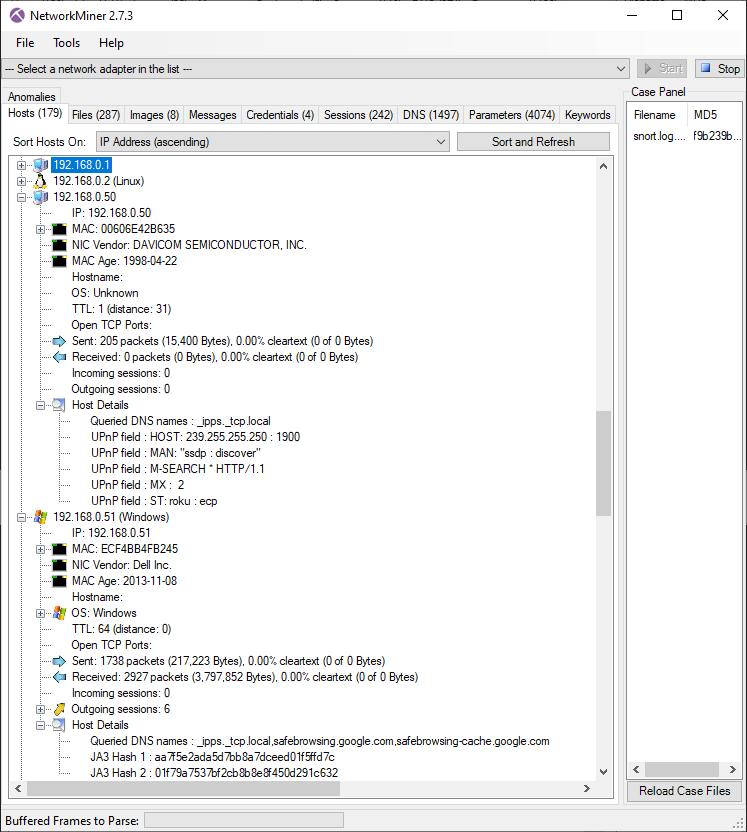
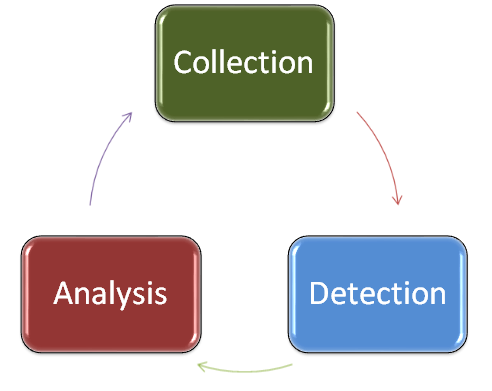
Applied Network Security Monitoring: Collection, Detection, and Analysis : Sanders, Chris, Smith, Jason: Amazon.de: Bücher

Wireshark & NSM Tools used for Incident Response & Threat Hunting - ISSA Grand Traverse Workshop 1/2 - YouTube

Applied Network Security Monitoring: Collection, Detection, and Analysis : Sanders, Chris, Smith, Jason: Amazon.de: Bücher

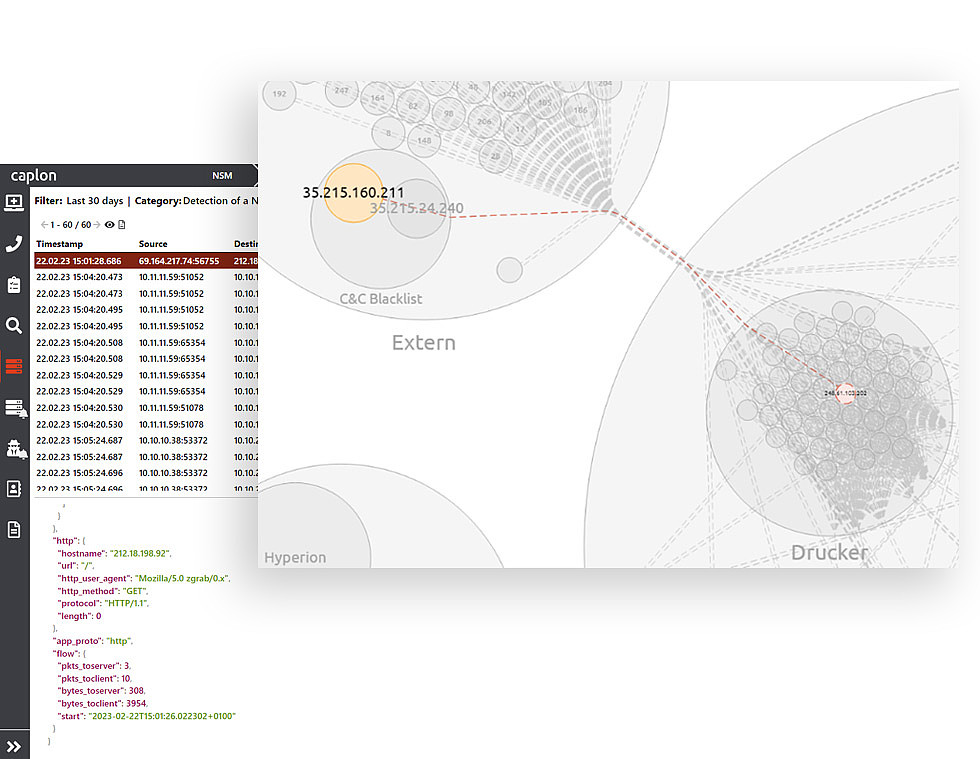
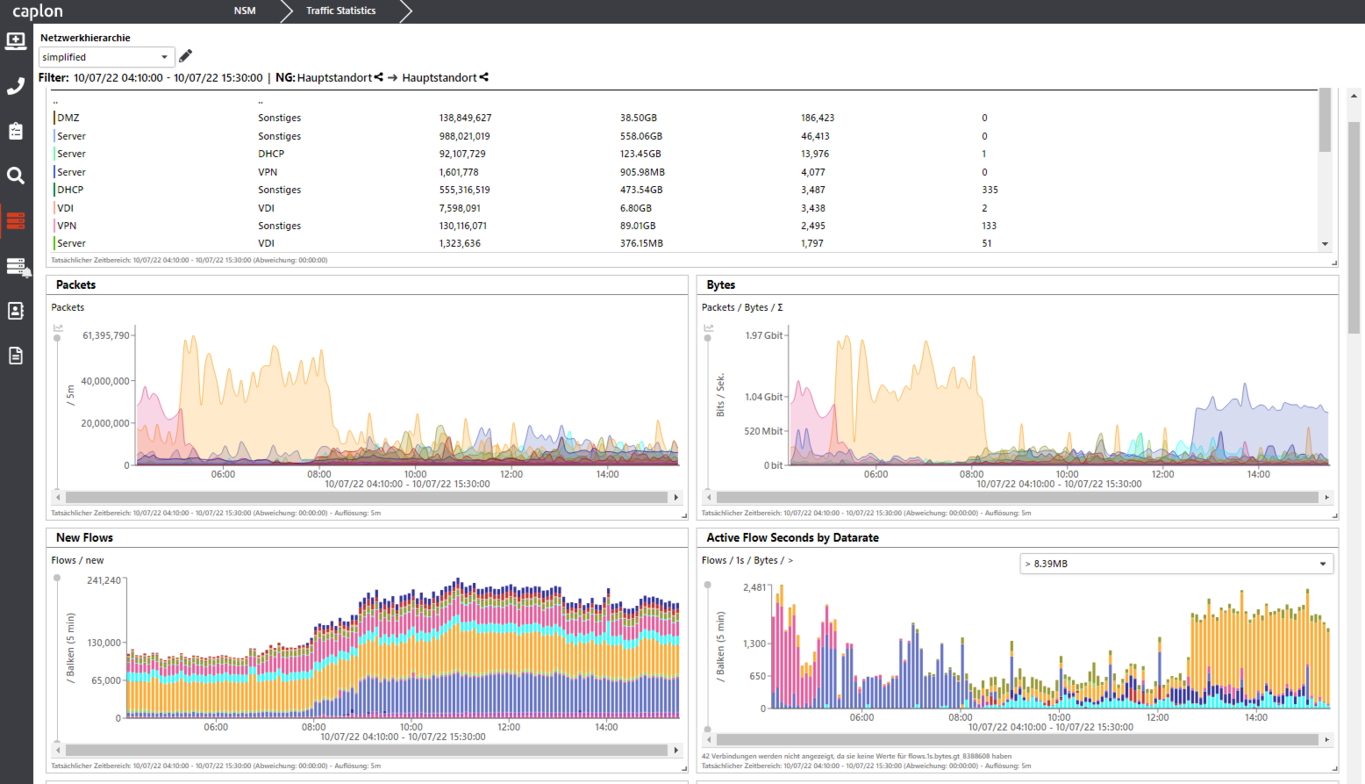
Checklist for Network Security Monitoring (NSM) for On-premise, Data Centers and Cloud set-ups – Detecting anomalous network patterns



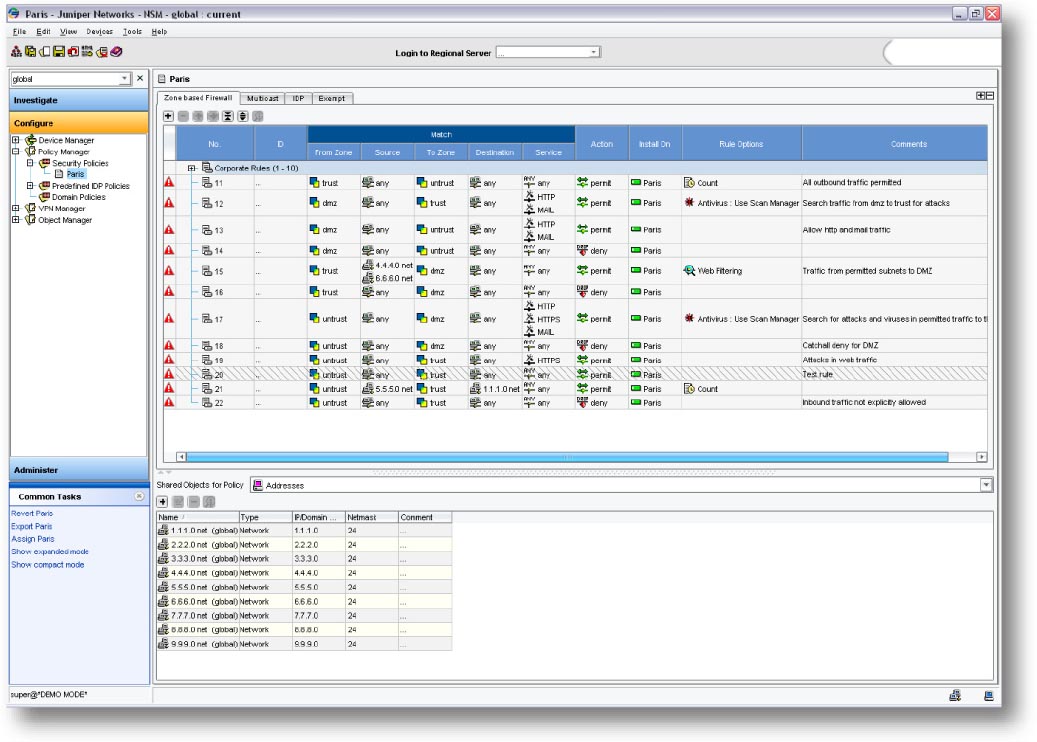





:quality(90)/p7i.vogel.de/wcms/78/0f/780fe7a3b5cd826c836b2fe8c1e9c5bb/0109811936.jpeg)