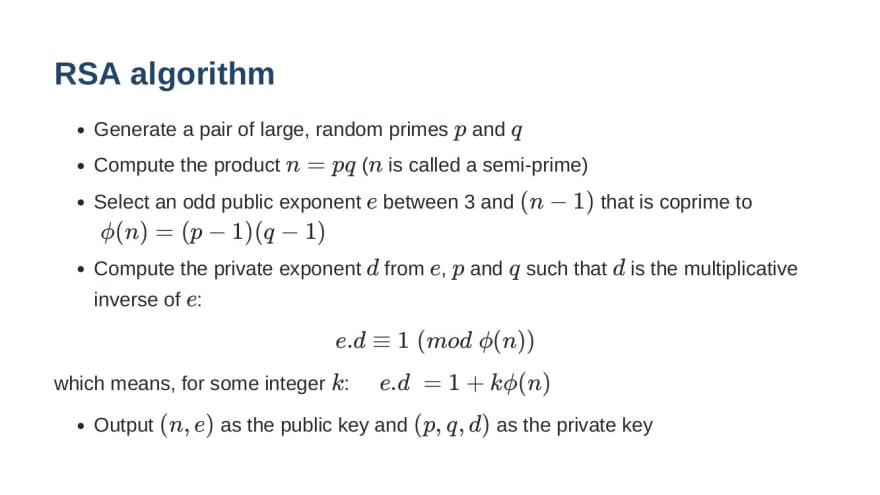
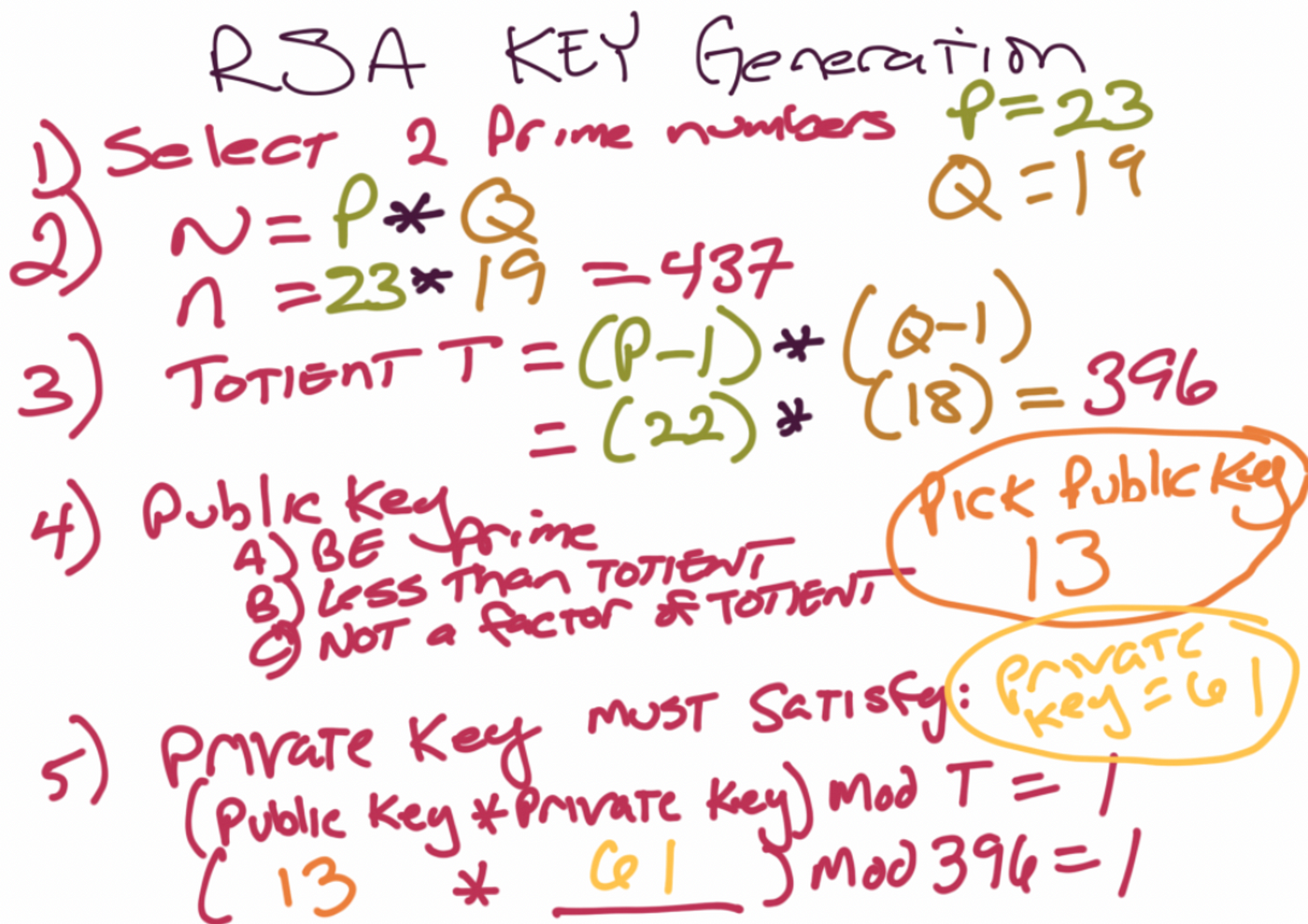
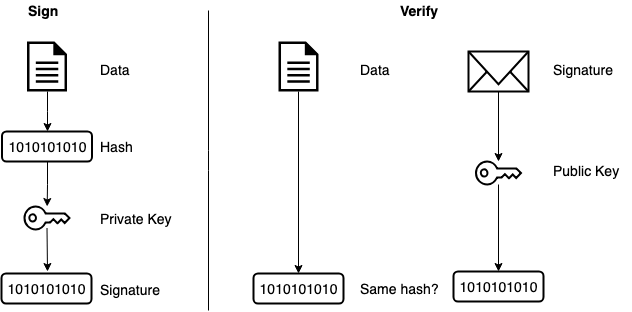
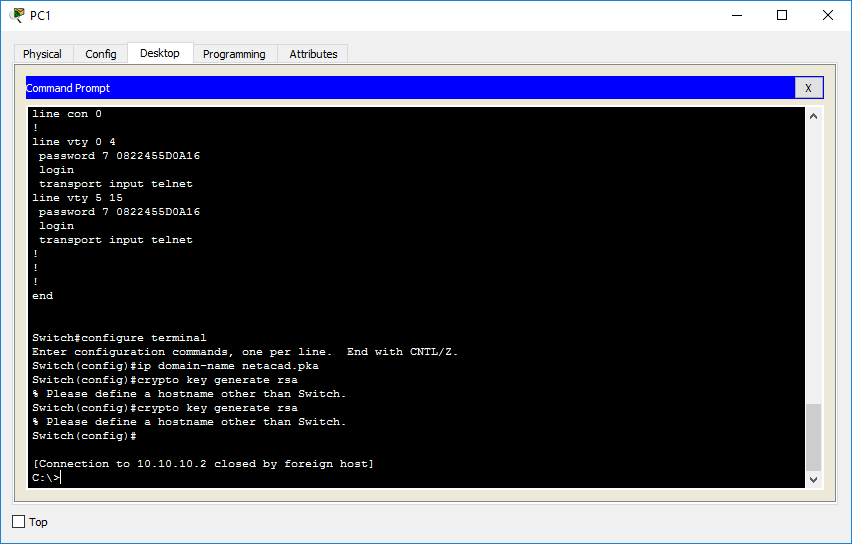
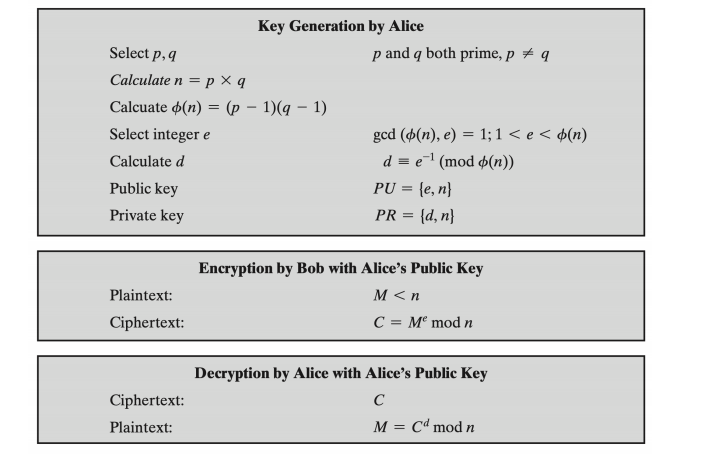
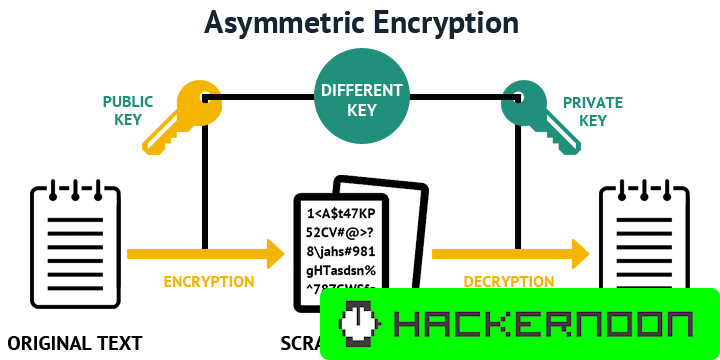
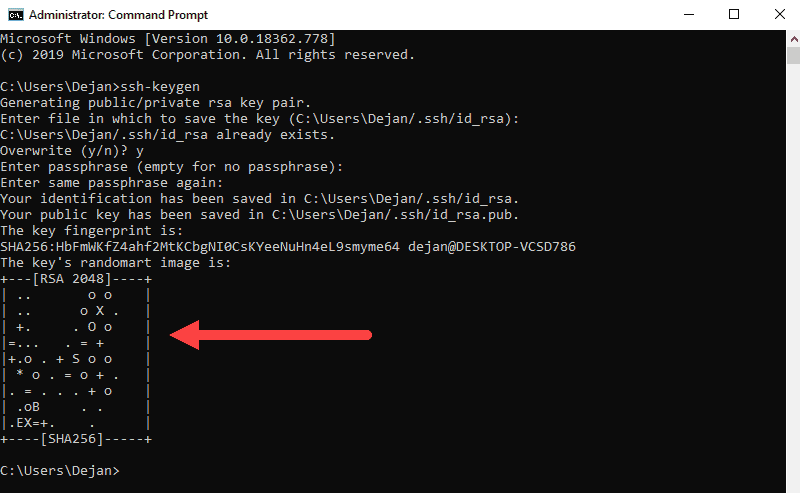
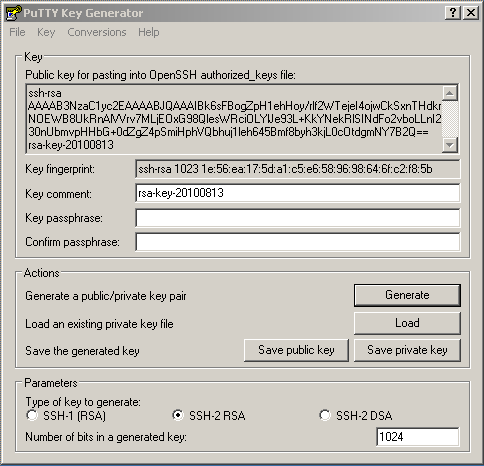
![PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3814d0ffa05d6c3afff2d829675b7be549b4cf40/11-Table3.2-1.png)
PDF] Efficient RSA Key Generation Protocol in a Two-Party Setting and its Application into the Secure Multiparty Computation Environment | Semantic Scholar
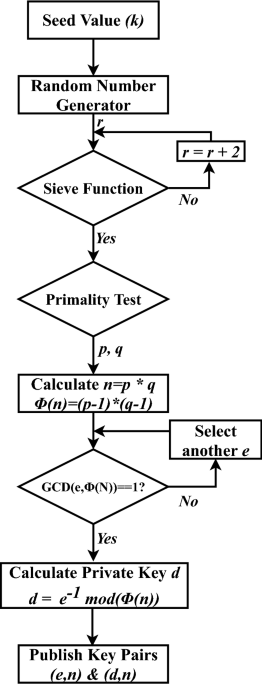
Two-factor-based RSA key generation from fingerprint biometrics and password for secure communication | Complex & Intelligent Systems
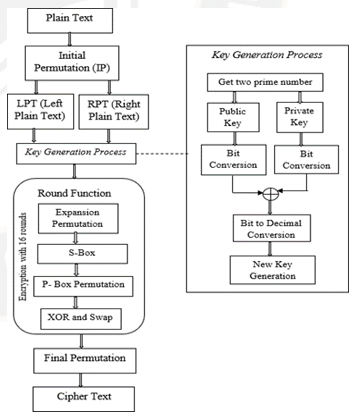
Moulded RSA and DES (MRDES) Algorithm for Data Security | International Journal on Recent and Innovation Trends in Computing and Communication