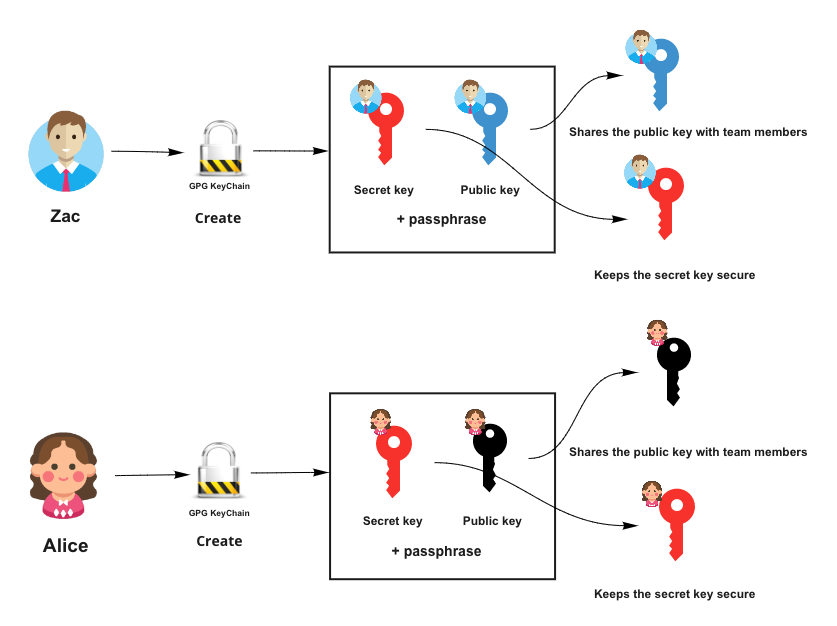
How to Use GPG to Securely Share Secrets with Your Team | by Sanjeev Nithyanandam | Slalom Build | Medium

Optimise building performance, reduce energy consumption and ensure compliance with our Energy Management GPG, in partnership with Carbon Numbers