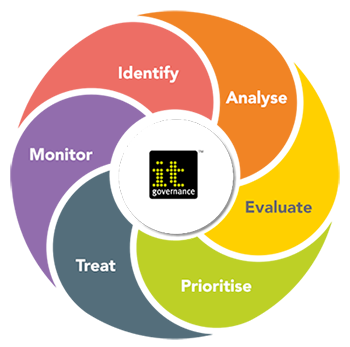
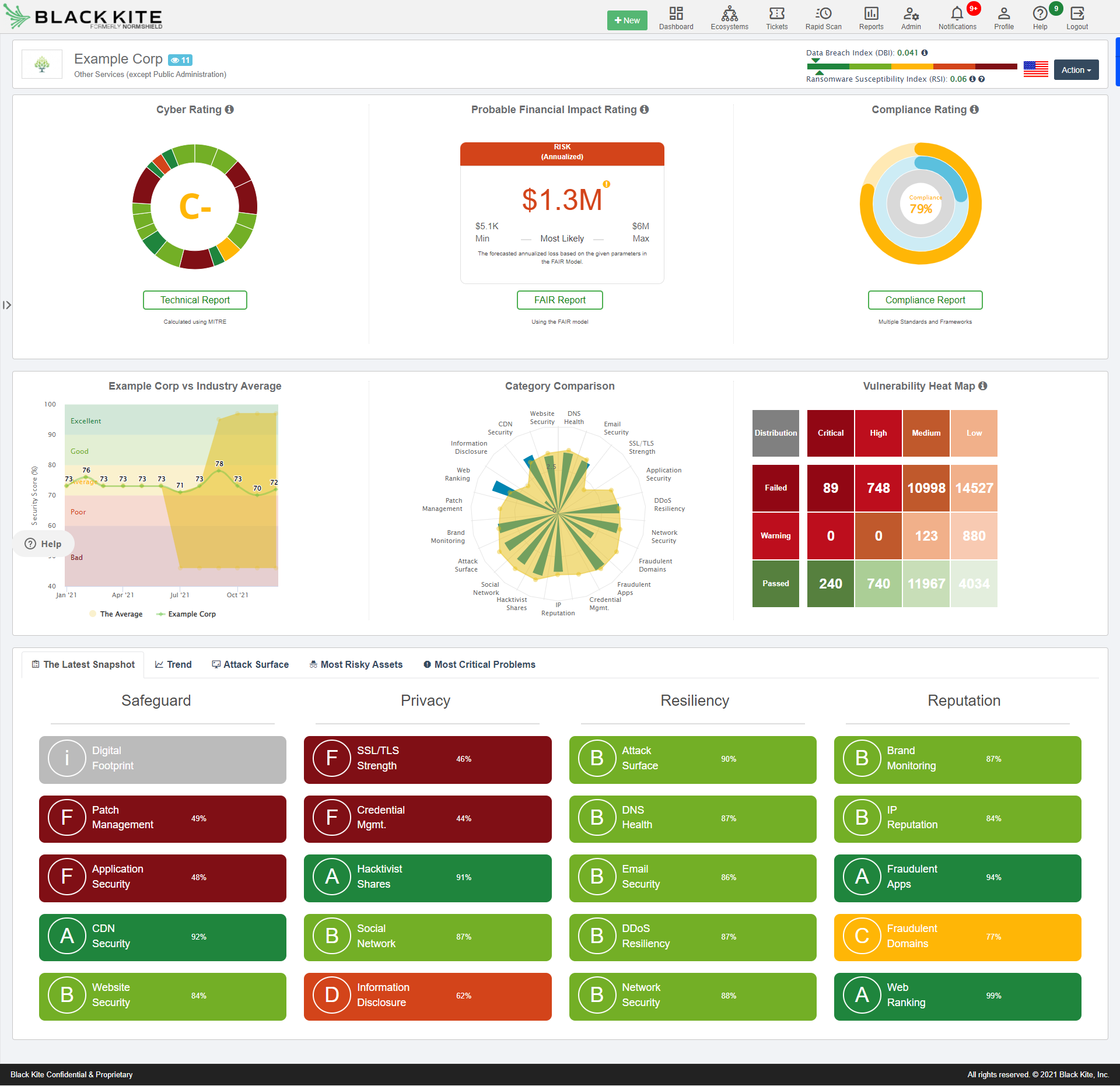
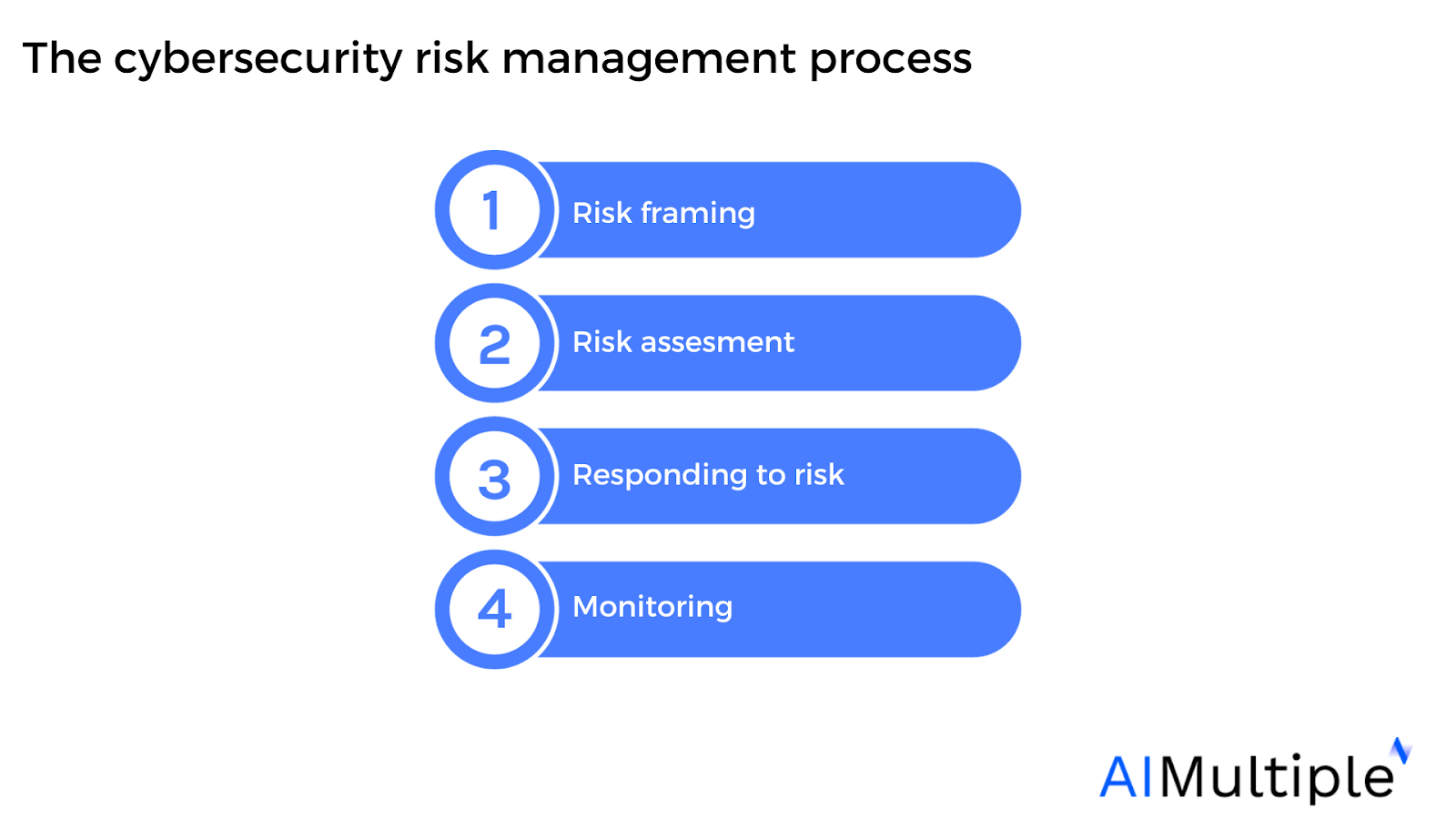
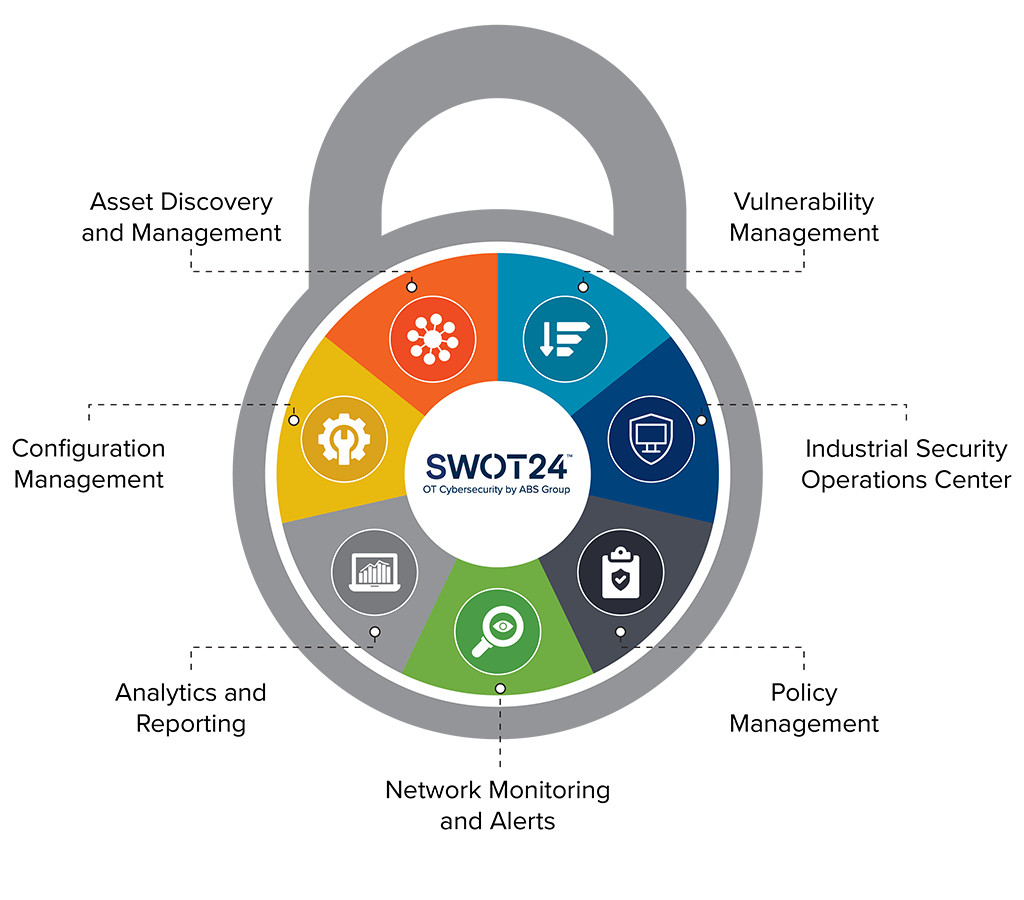
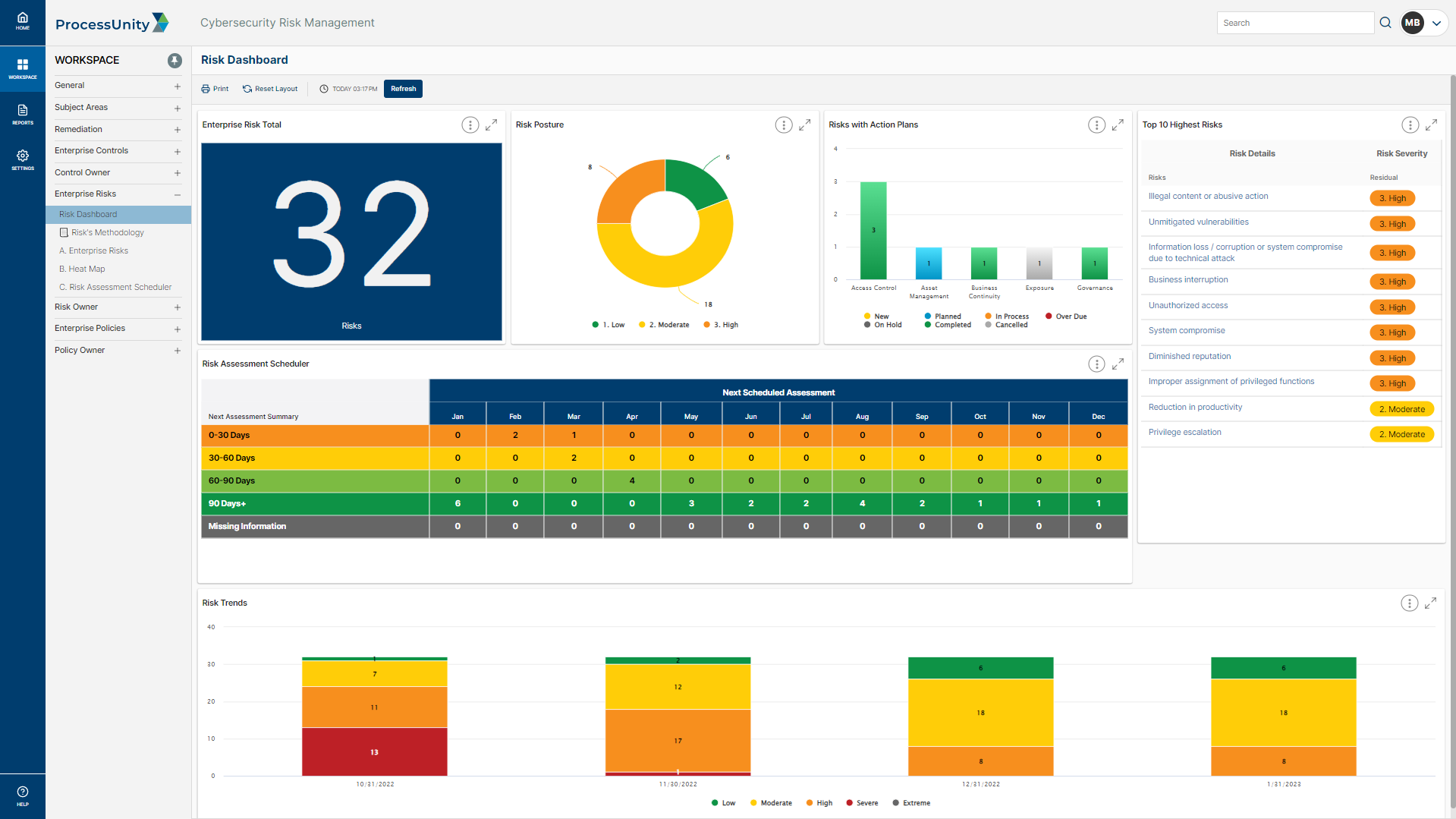
Navigating the Lifecycle of Cyber Risk Management: A Strategic Blueprint | by Juan Pablo Castro | Feb, 2024 | Medium
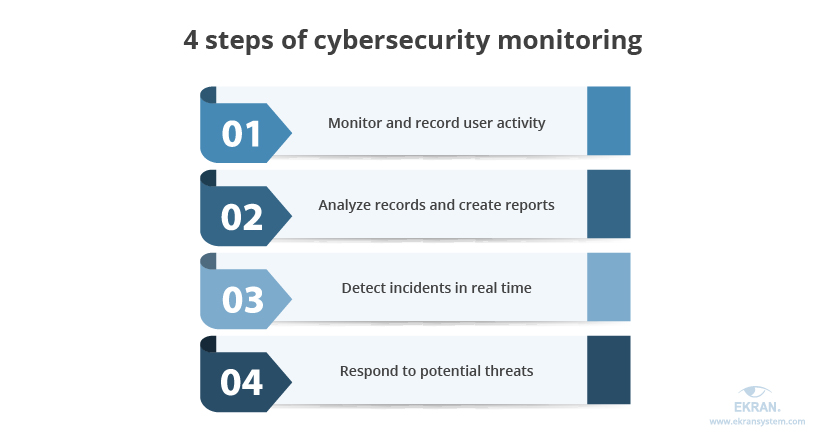
4 Steps to Ensuring Efficient Cybersecurity Monitoring in US Educational Institutions | Ekran System

Systemic cyber risk management for enterprise network. The asset owner... | Download Scientific Diagram
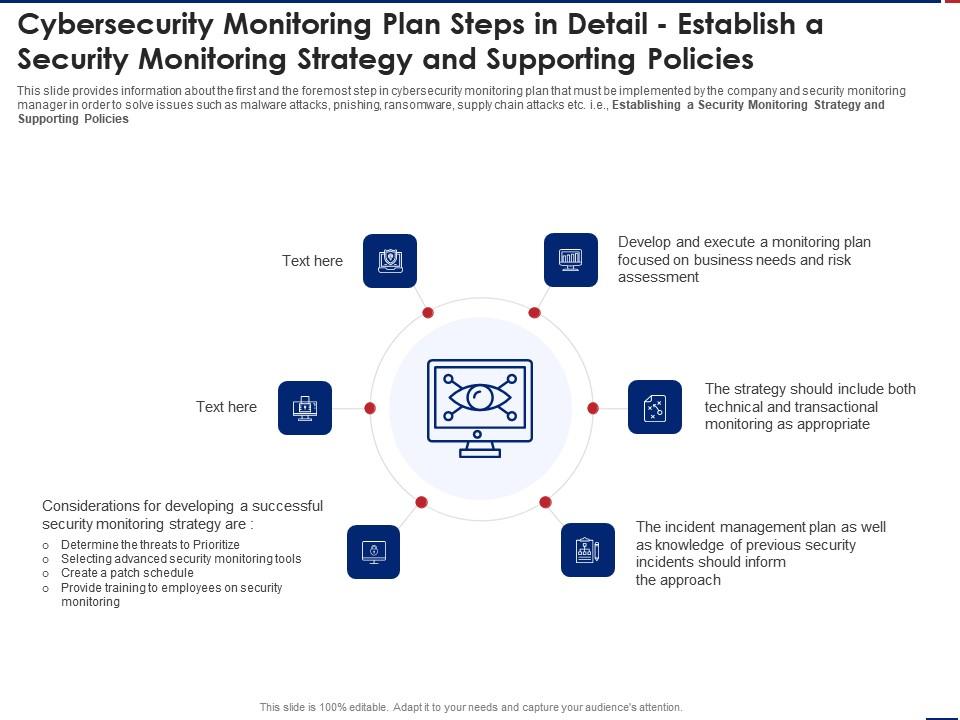
Effective Security Monitoring Plan Cybersecurity Monitoring Strategy Ppt Pictures | Presentation Graphics | Presentation PowerPoint Example | Slide Templates