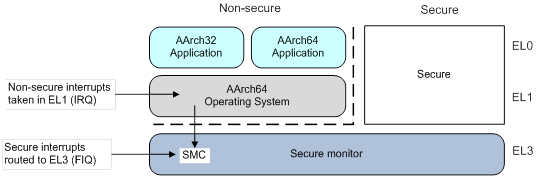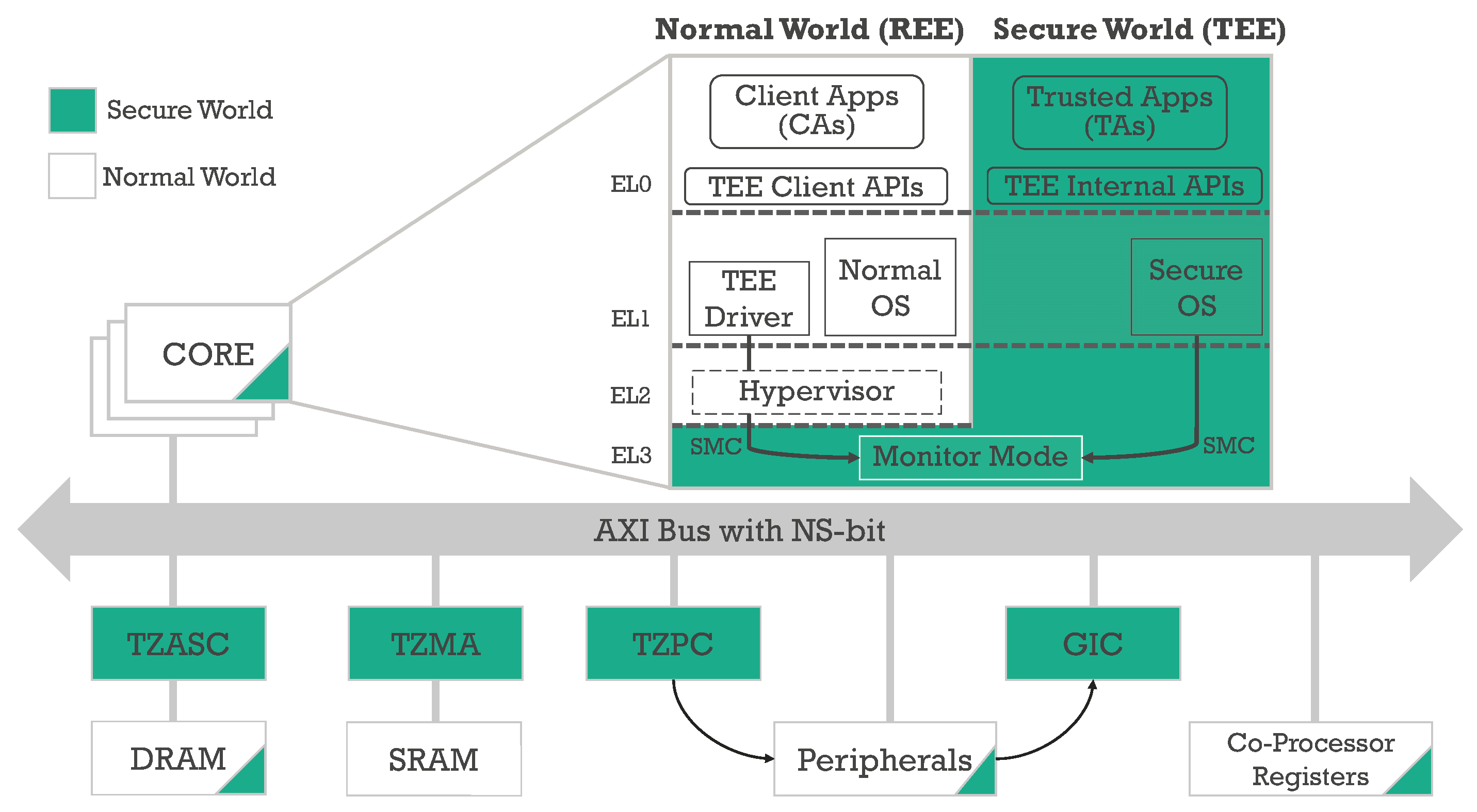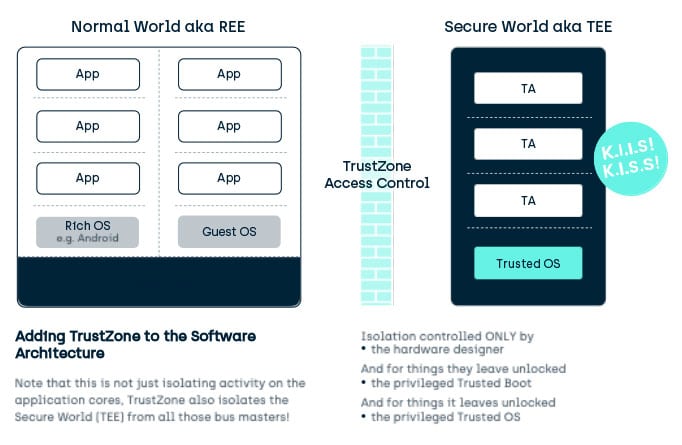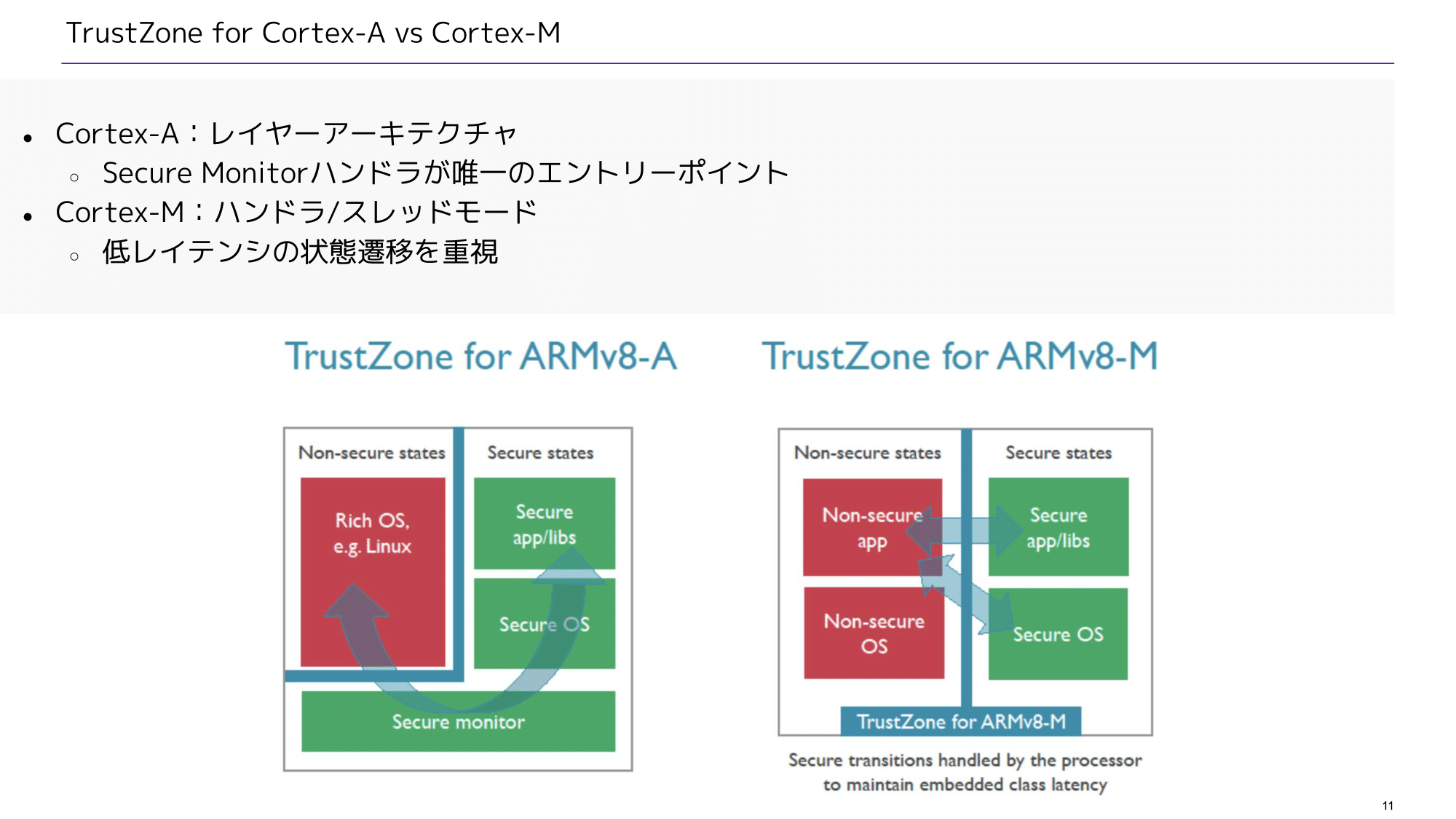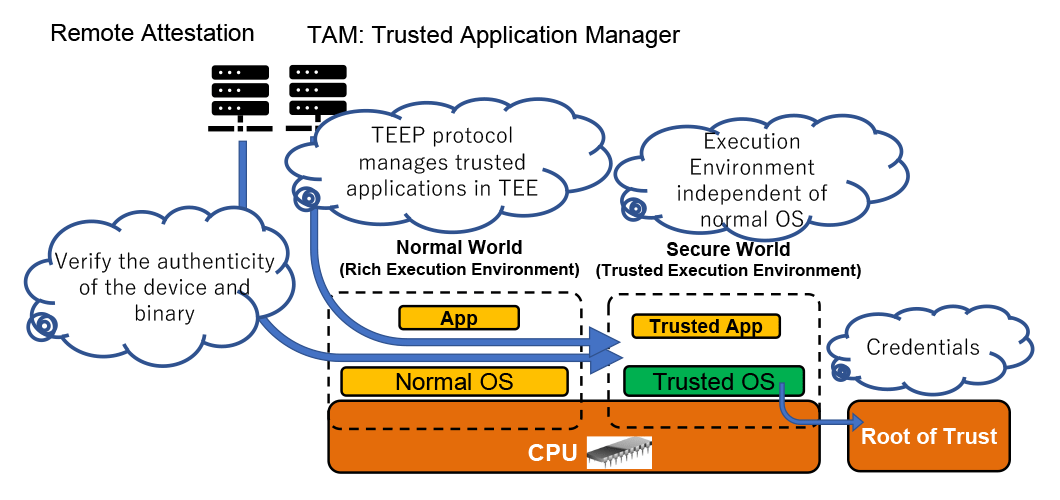
TEE (Trusted Execution Environment) and its supporting technologies | Cryptography Platform Research Team | Cyber Physical Security Research Center - AIST
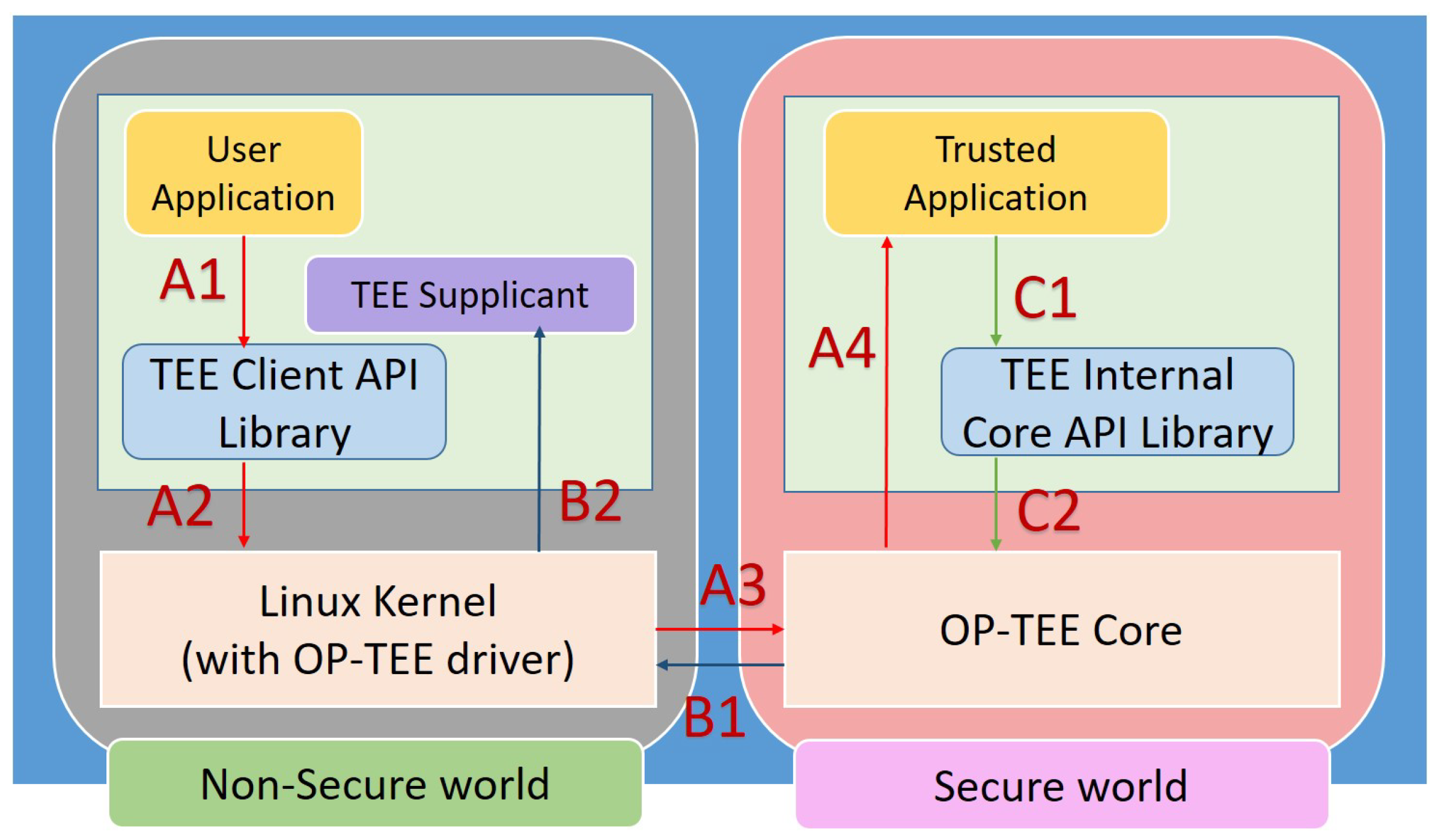
Sustainability | Free Full-Text | STBEAT: Software Update on Trusted Environment Based on ARM TrustZone

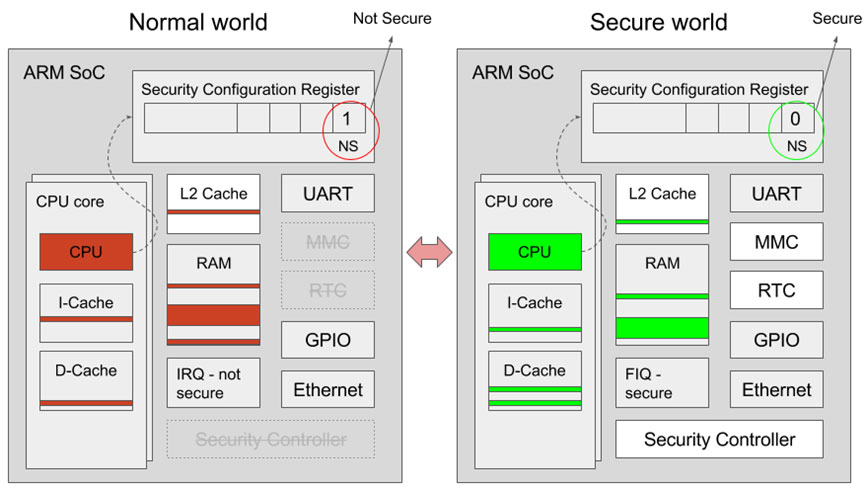
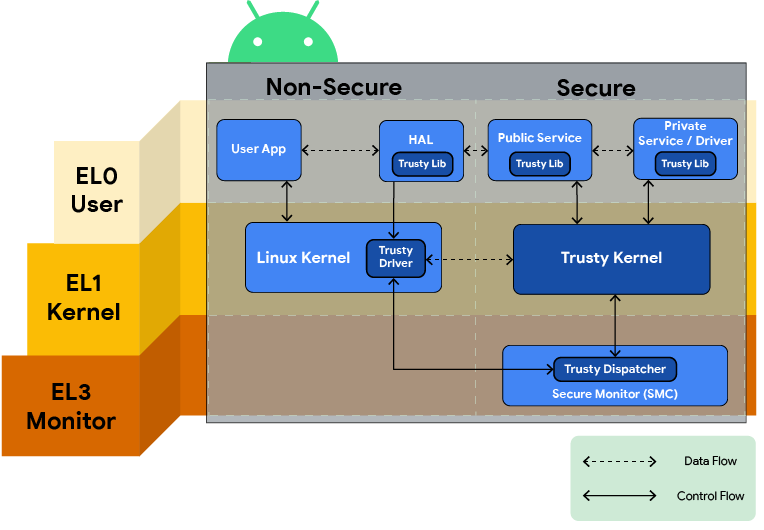
![PDF] vTZ: Virtualizing ARM TrustZone | Semantic Scholar PDF] vTZ: Virtualizing ARM TrustZone | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bad6552f0b3e533194c9c1d8a26a5fd470b1b24d/6-Figure2-1.png)
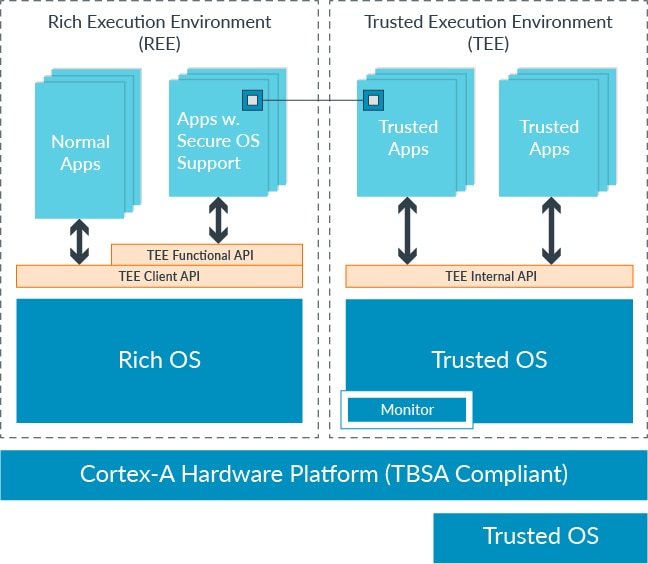
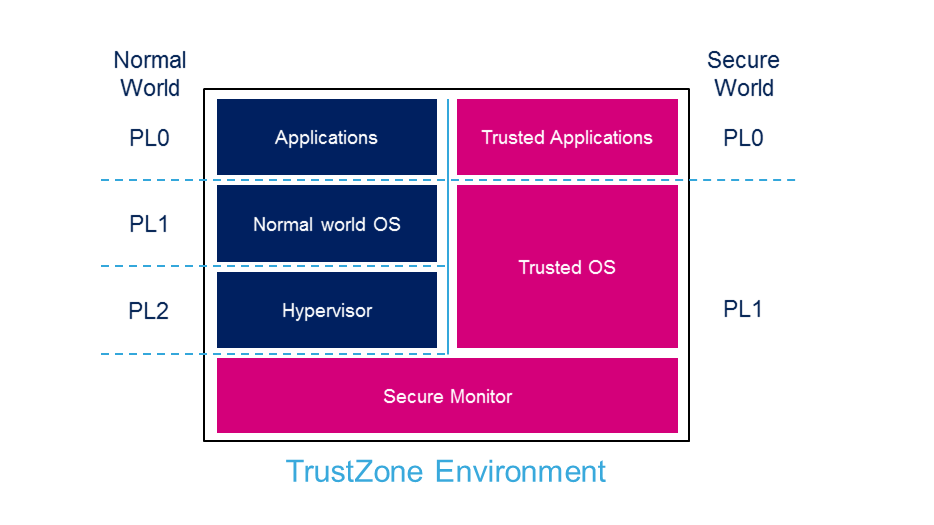
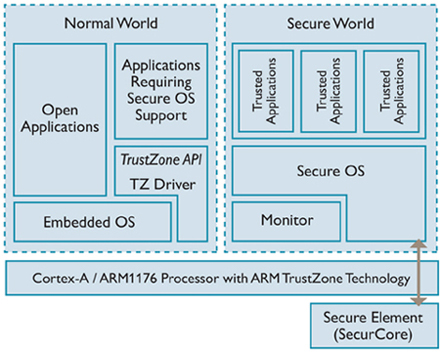
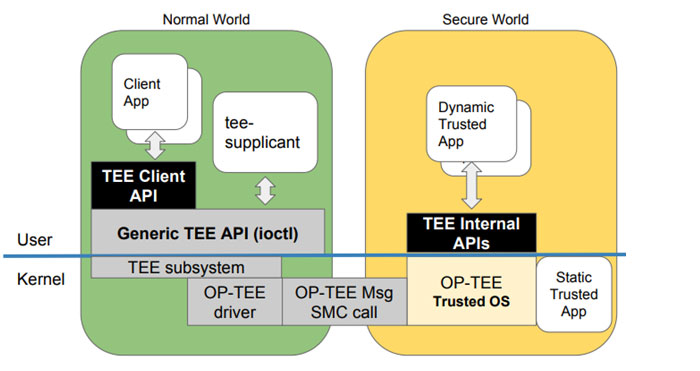
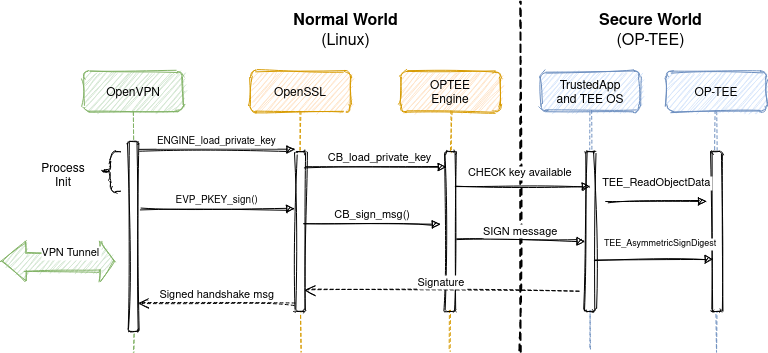
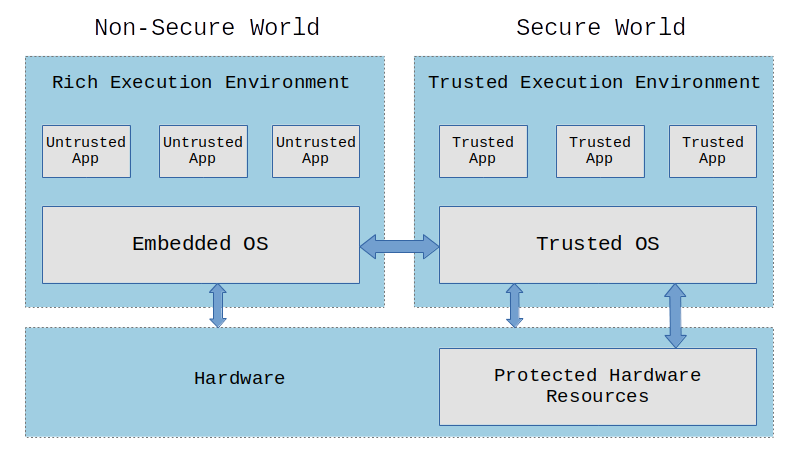

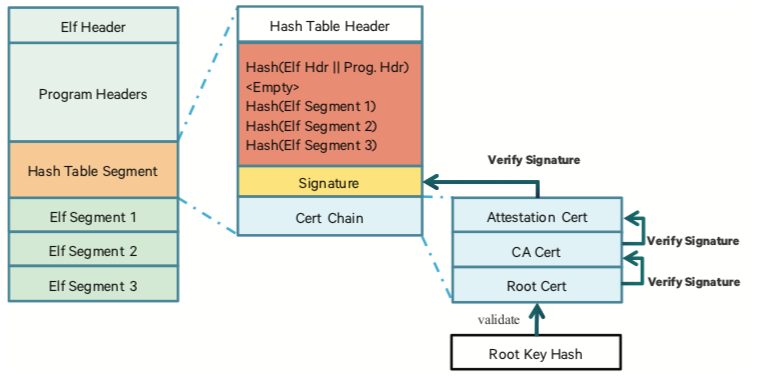

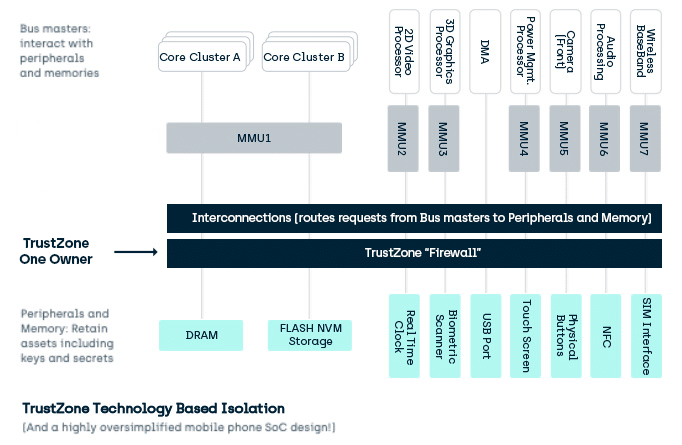

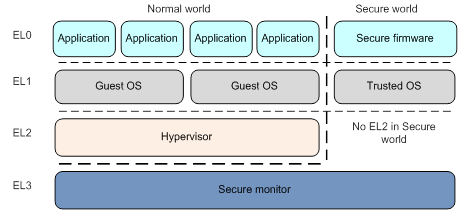
![ARM TrustZone: A Crash Course for Reversers | by Path Cybersec [Slava Moskvin] | Medium ARM TrustZone: A Crash Course for Reversers | by Path Cybersec [Slava Moskvin] | Medium](https://miro.medium.com/v2/resize:fit:685/1*2YMDyQ8z_kjbyR8N9qf6kA@2x.jpeg)