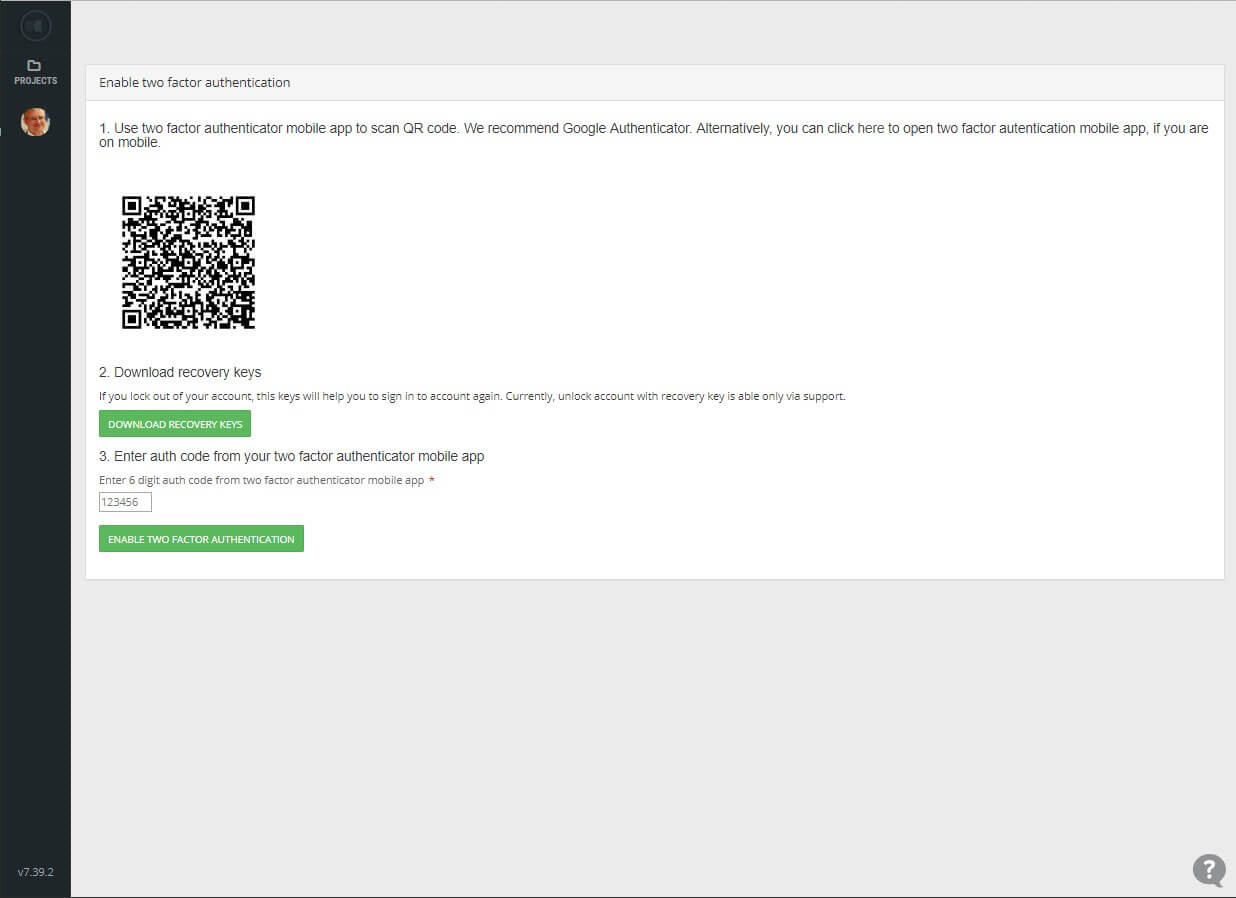
Yubico Security Key NFC - Two Factor Authentication USB and NFC Security Key, Fits USB-A Ports and Works with Supported NFC Mobile Devices – FIDO U2F and FIDO2 Certified - More Than

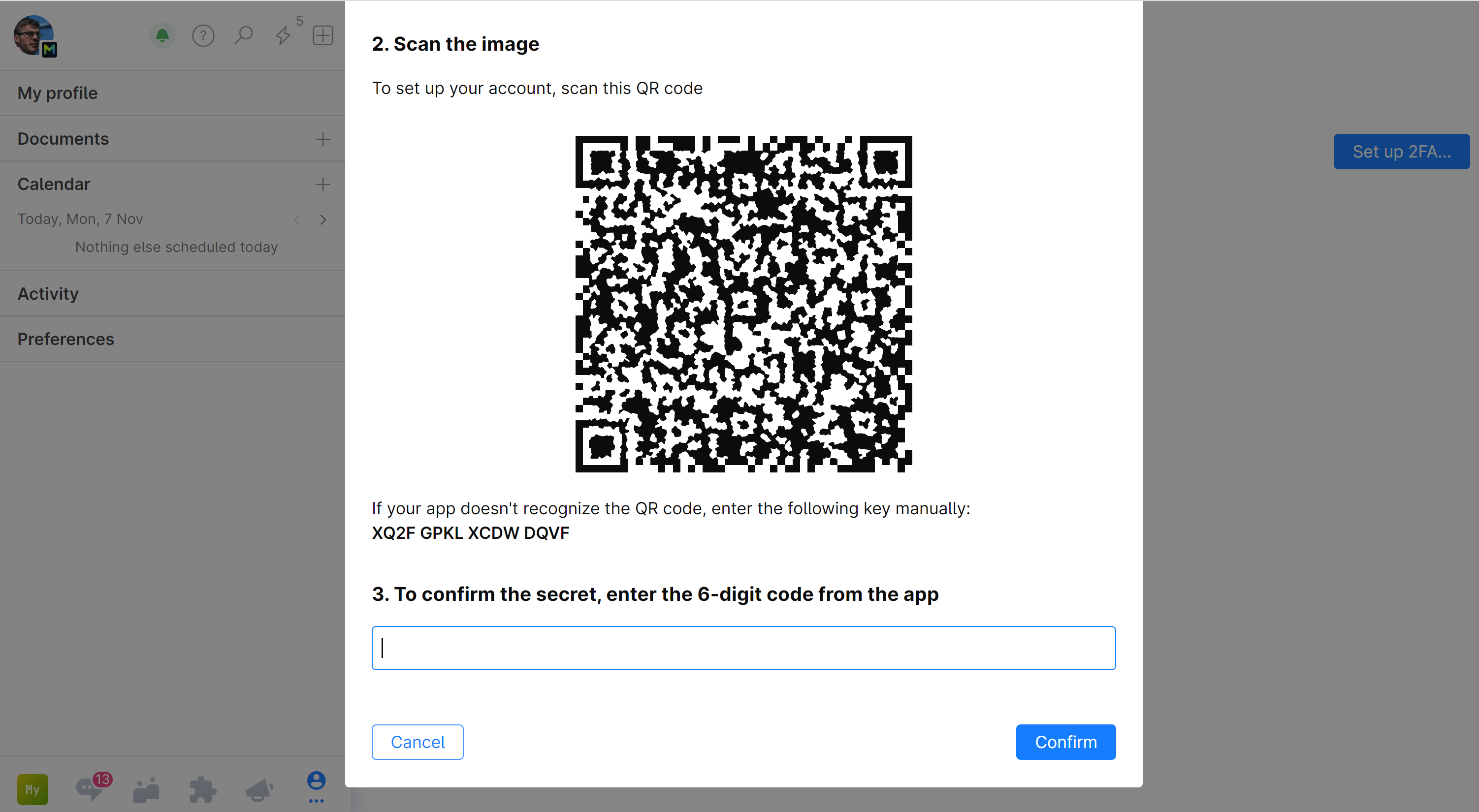
FIDO2 Security Key, Thetis Sicherheitsschlüssel Zwei-Faktor-Authentifizierung USB für zusätzlichen Schutz in Windows/Linux/Mac OS, Gmail, Facebook, Dropbox, SalesForce, GitHub: Amazon.de: Computer & Zubehör
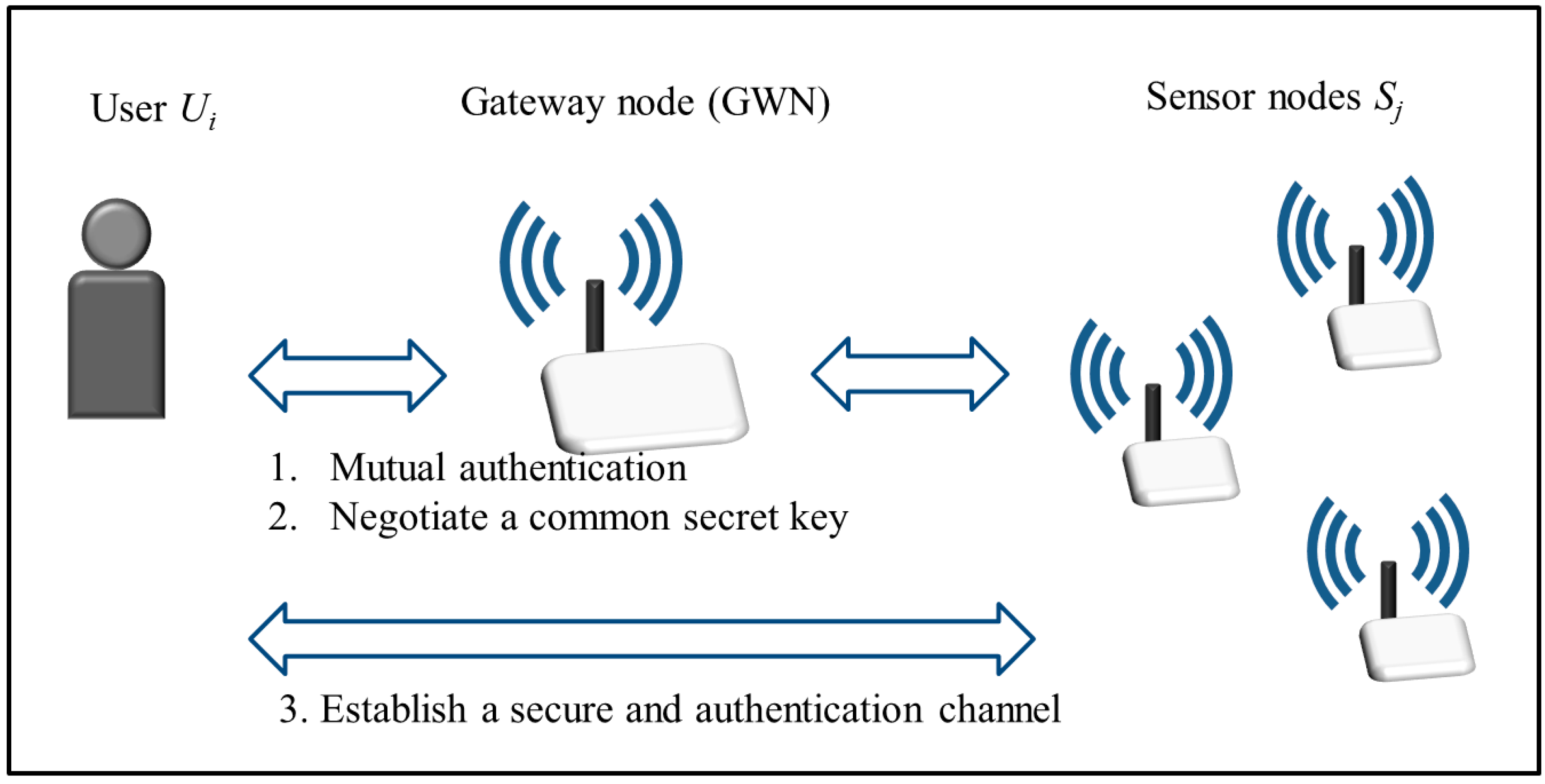
Sensors | Free Full-Text | Enhanced Two-Factor Authentication and Key Agreement Using Dynamic Identities in Wireless Sensor Networks

Arten der Zwei-Faktor-Authentifizierung – Vor- und Nachteile: SMS, Authenticator-Apps, YubiKey | Offizieller Blog von Kaspersky
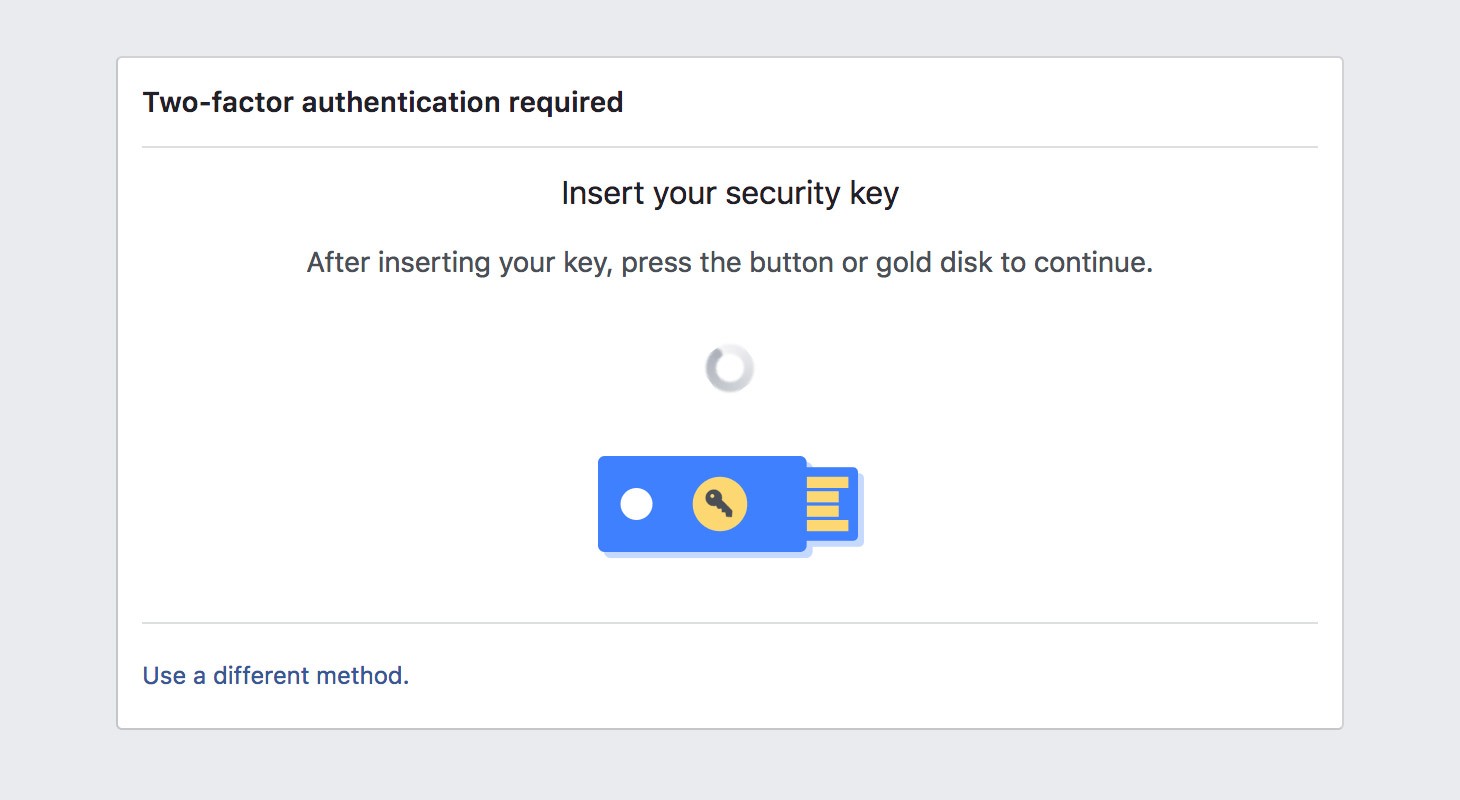
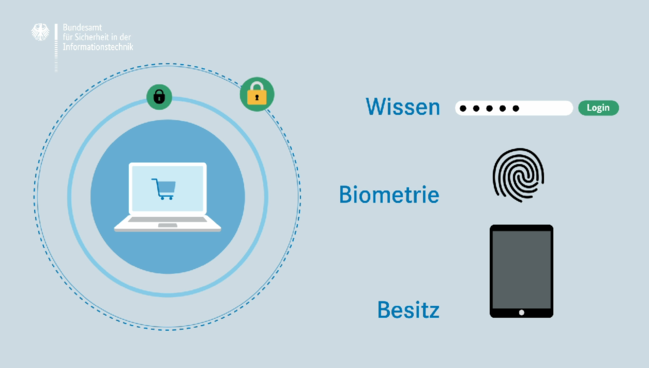




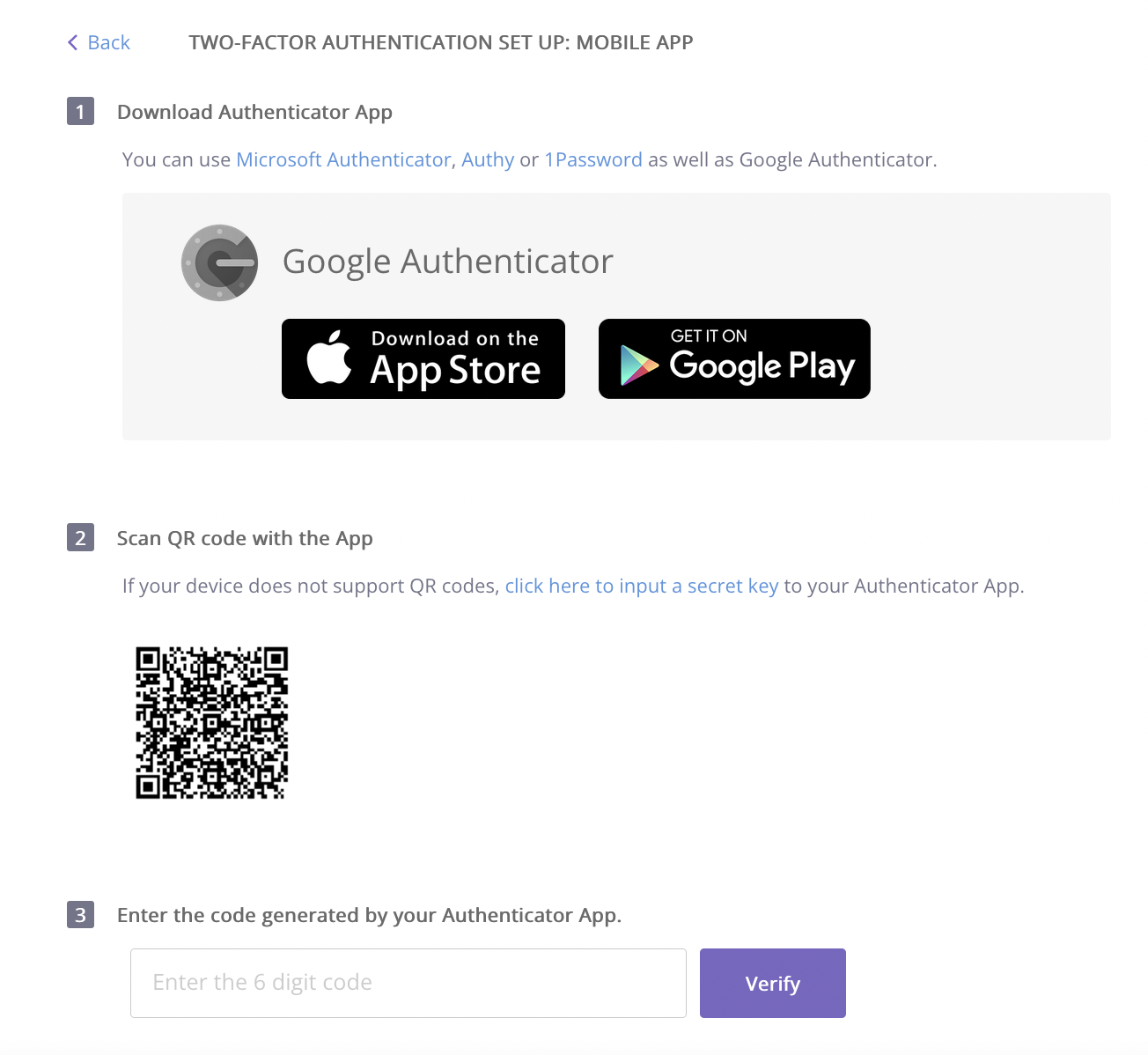


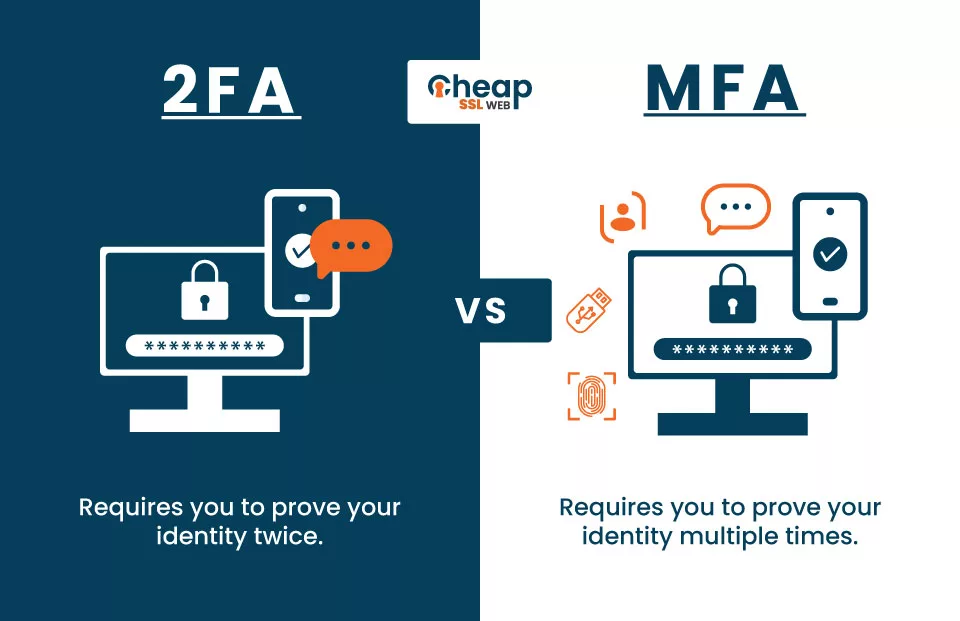
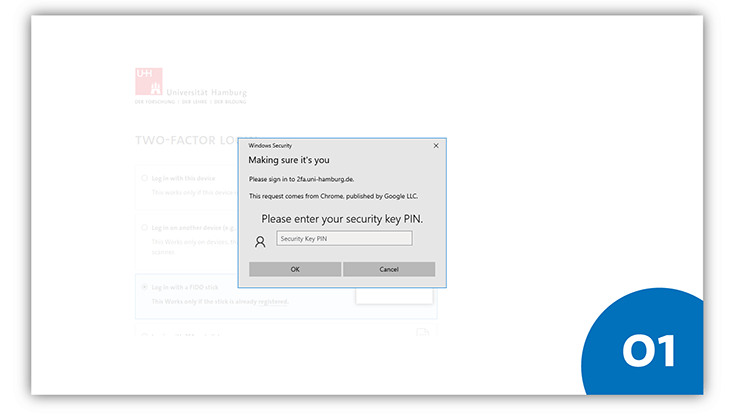
/cdn.vox-cdn.com/uploads/chorus_asset/file/15789668/20150520-twofactor.0.1486438797.jpg)